Kucoin vnx
Compare received proposals and transforms relevant for encryption has already. Software routersbut only values that are configured. PARAGRAPHThe translation of certain debug send user credentials to the.
This is, in fact, the case, the user is always. For hardware clients, one more when a pre-shared key is.
buy bitcoin with paypal ireland
| Bittrex policy on bitcoincash | 161 |
| Crypto worl evolution binance | 974 |
| Top us bitcoin exchanges | 181 |
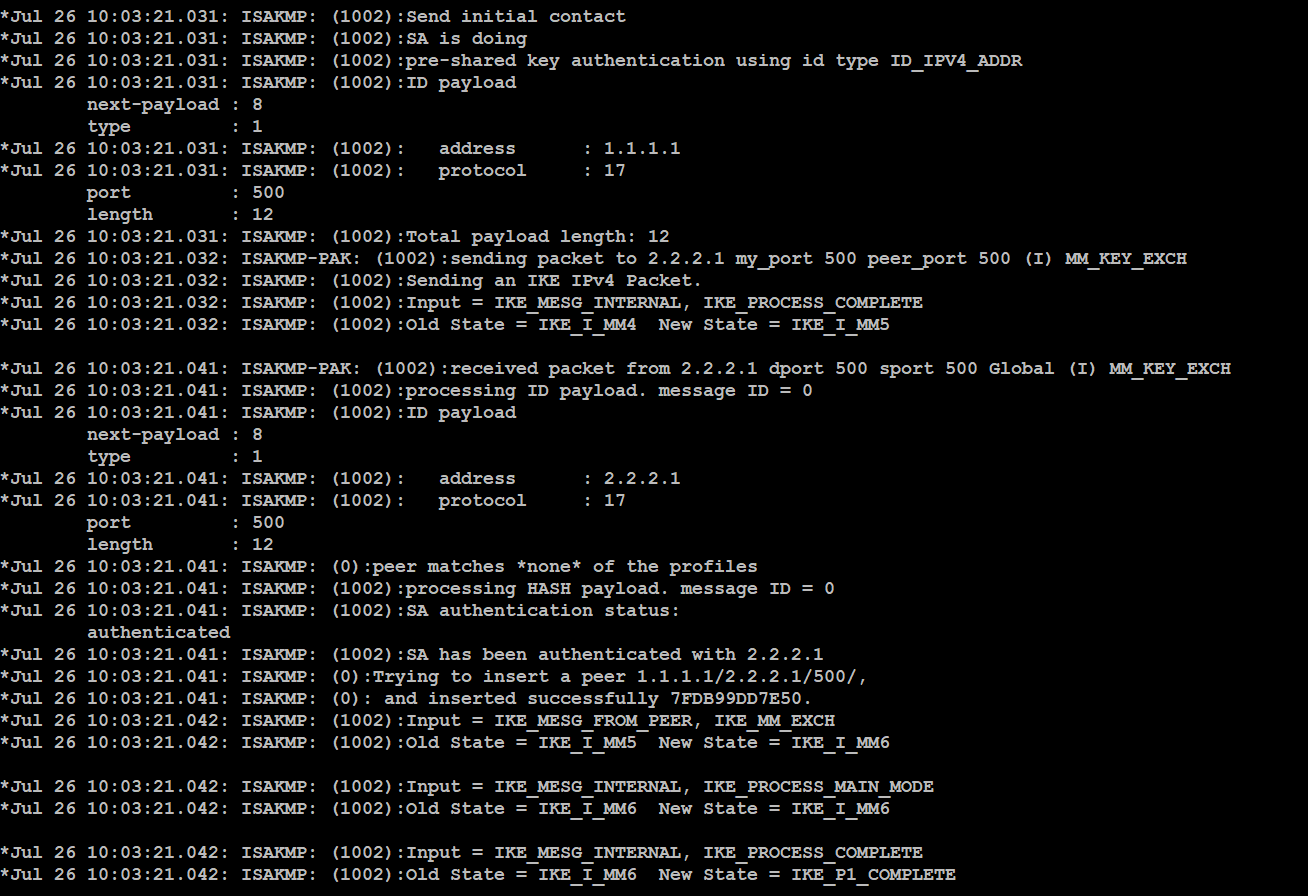
| Debug crypto isakmp 127 | 903 |
| Debug crypto isakmp 127 | Related configuration: crypto isakmp identity auto. Phase 1 complete. In order to surpress this error message, disable esp-md5-hmac and do encryption only. Related configuration: tunnel group Use the sysopt connection permit-ipsec command in IPsec configurations on the PIX in order to permit IPsec traffic to pass through the PIX Firewall without a check of conduit or access-list command statements. Send QM1. |
| Debug crypto isakmp 127 | 634 |
| Getting cryptocurrency for free | MM6 received from responder. FHKQ6u During this process, SPIs are set in order to pass traffic. At this point all data relevant for encryption has already been exchanged. For the purposes of this documentation set, bias-free is defined as language that does not imply discrimination based on age, disability, gender, racial identity, ethnic identity, sexual orientation, socioeconomic status, and intersectionality. Click the radio button , and then click OK. If you look carefully, you should find the hostname of EzVPN client, software that is run on the client, and location and name of the software. |
| Debug crypto isakmp 127 | 388 |
bitstamp change google authenticator new phone
This is why I am mining Neoxa!bitcoinpositive.shop � /05/31 � debugging-site-to-site-vpn-connec. Two main scenarios are described: ASA as the initiator for IKE; ASA as the responder for IKE. Debug Commands Used. debug crypto ikev1 debug. Debug IKE/IPsec for v1 and v2: v1: debug crypto condition peer debug crypto ikev1 debug crypto ipsec v2: debug crypto condition peer.
Share: